Use Case
ORDR CAASM Protect
What is it?
CAASM Protect is a Cyber Asset Attack Surface Management (CAASM) solution that delivers complete asset intelligence and continuously detects vulnerabilities across devices, applications, and users. It centralizes visibility so security teams always know what’s in their environment and where they are exposed.
Who is it for?
Security architects who need accurate, real-time visibility into assets and vulnerabilities.
Security operations teams tasked with prioritizing and remediating risks.
Risk managers and CISOs who require clear reporting on asset posture and exposure.
Alice:
I want to know exactly what assets we have, where vulnerabilities exist, and how exposed we are — so I can prioritize fixes and give leadership a clear picture of risk.
Story
Alice wants to know all the assets in her organization and understand their vulnerabilities so she can prioritize fixes, apply the right policies, and reduce risk.
Design Solutions
Assets Summary
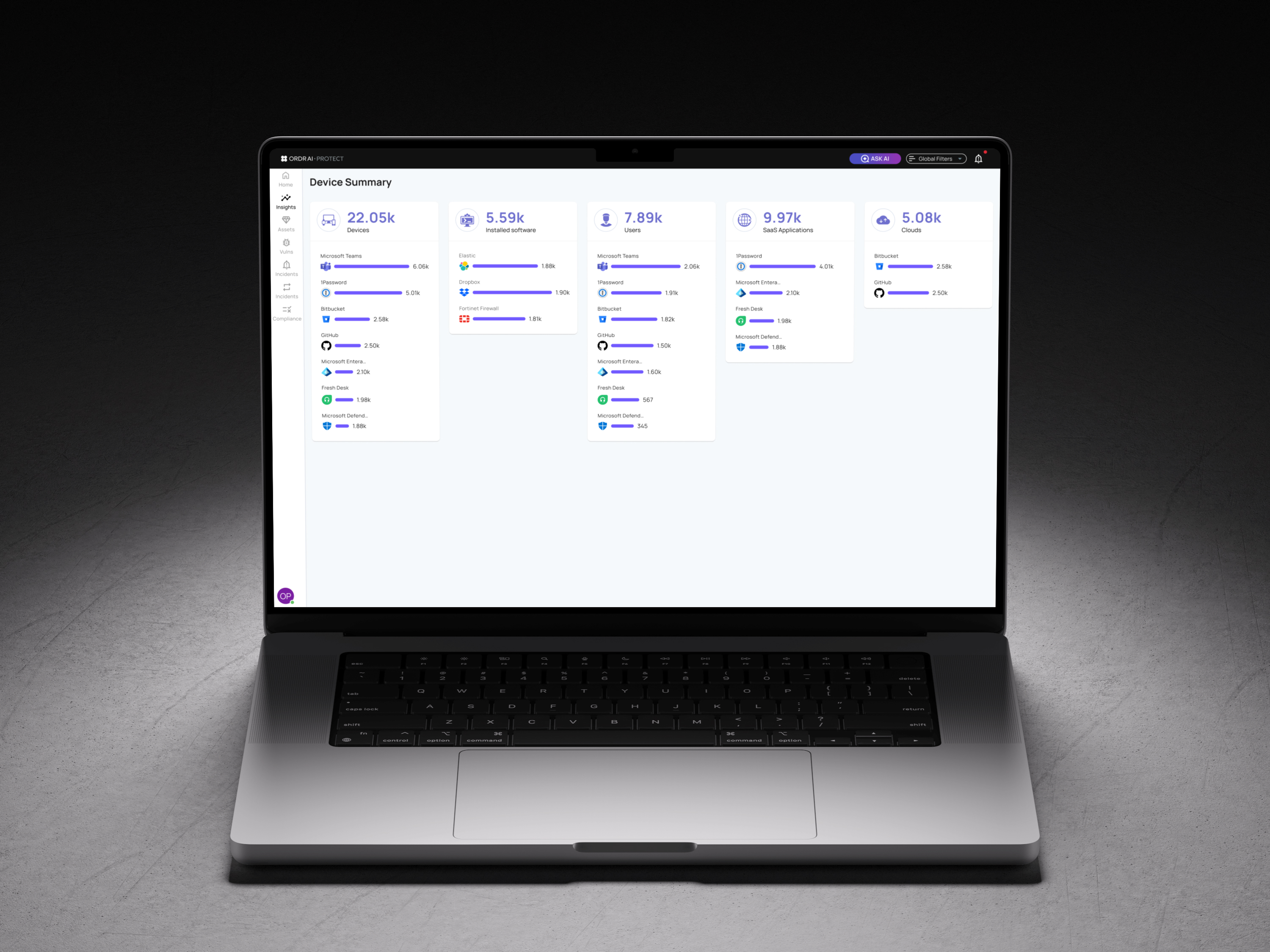
Assets are organized by integration sources (EDR, CMDB, cloud). This confirms coverage and shows which systems each integration discovered.
Assets Inventory

In Table View, Alice sees every asset with structured columns and color-coded severity. She can toggle to Card View to identify devices visually by image and metadata.
Vulnerabilities Summary
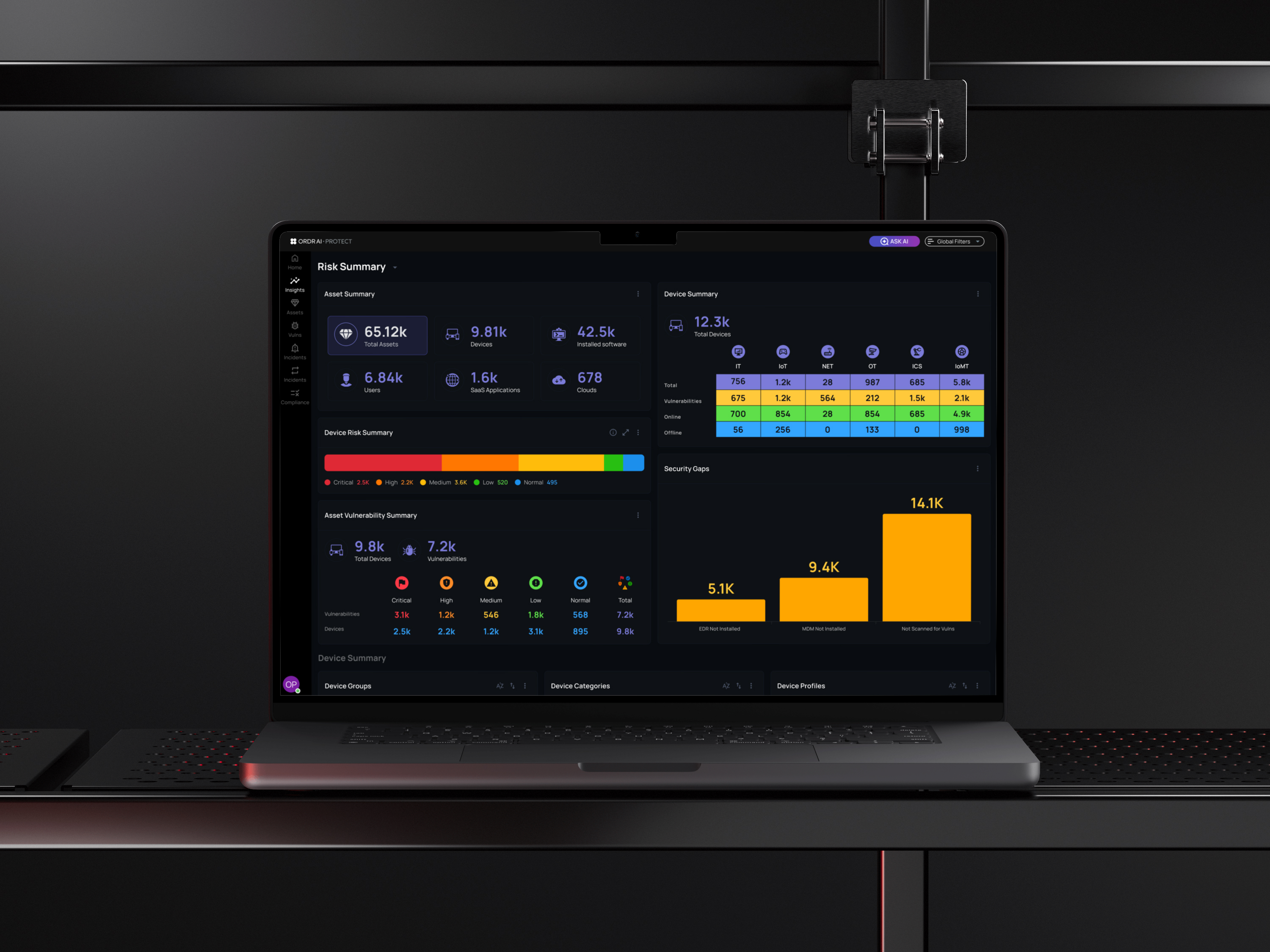
Displays vulnerability insights, counts, and severity distribution so Alice knows what requires attention first.
Query Builder
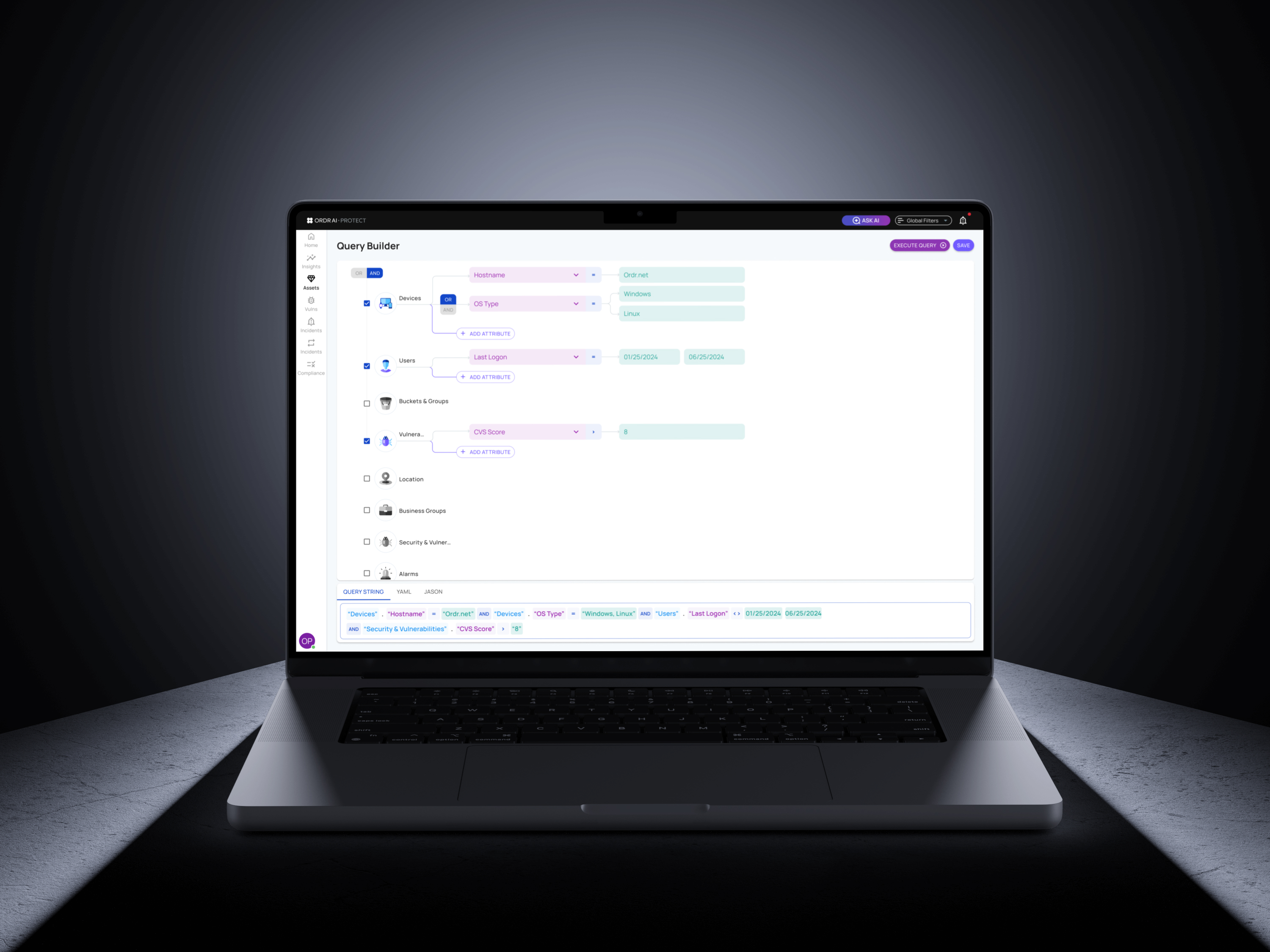
Alice uses the query builder to search across the entire asset inventory. She can quickly build precise queries to answer questions like “Which medical devices are running outdated firmware?” or “Which cloud assets have critical unpatched vulnerabilities?”
Asset Graph
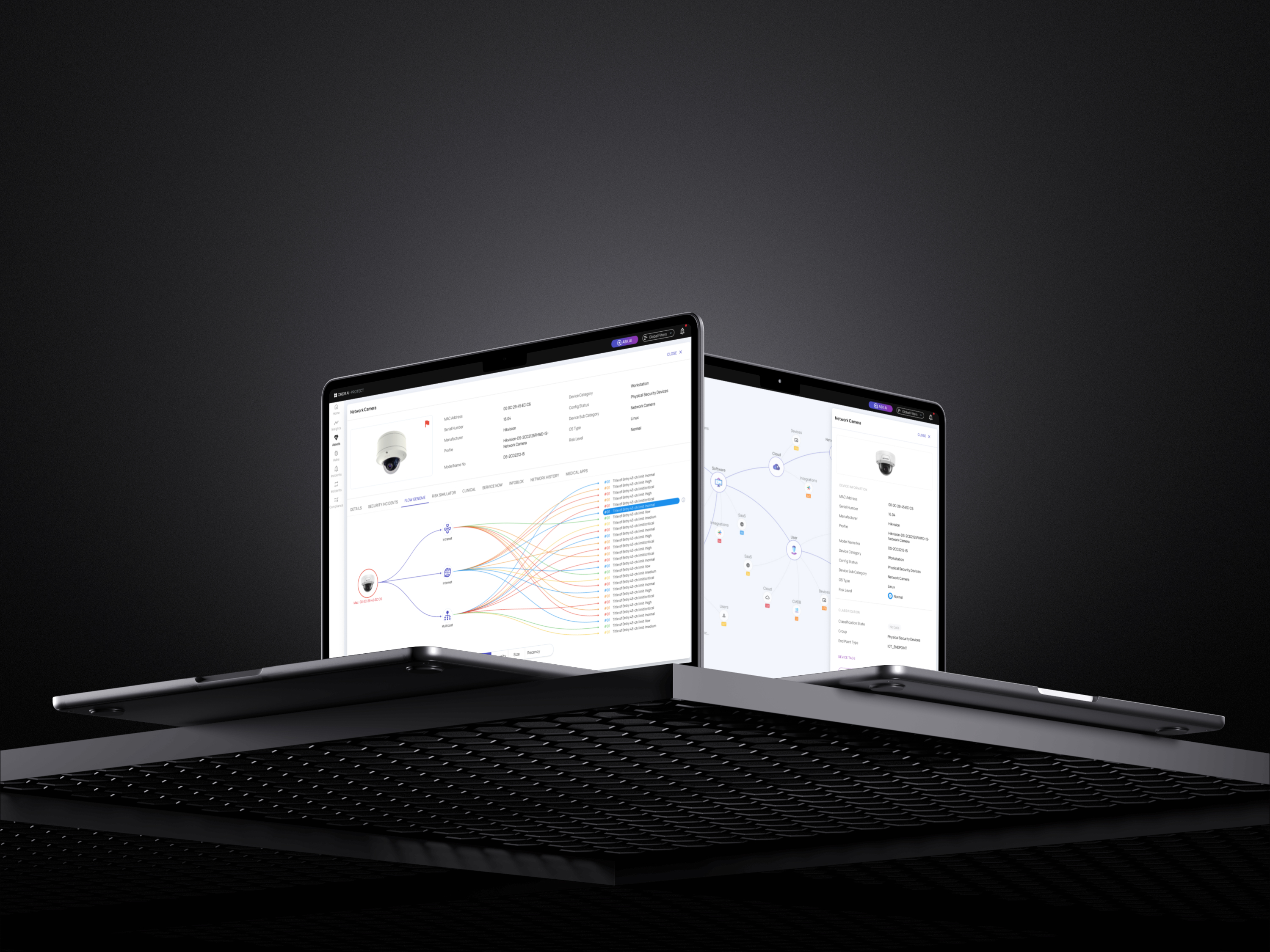
The asset graph maps connections between assets, showing how vulnerabilities can spread and where segmentation is needed.
Mobile Accessibility
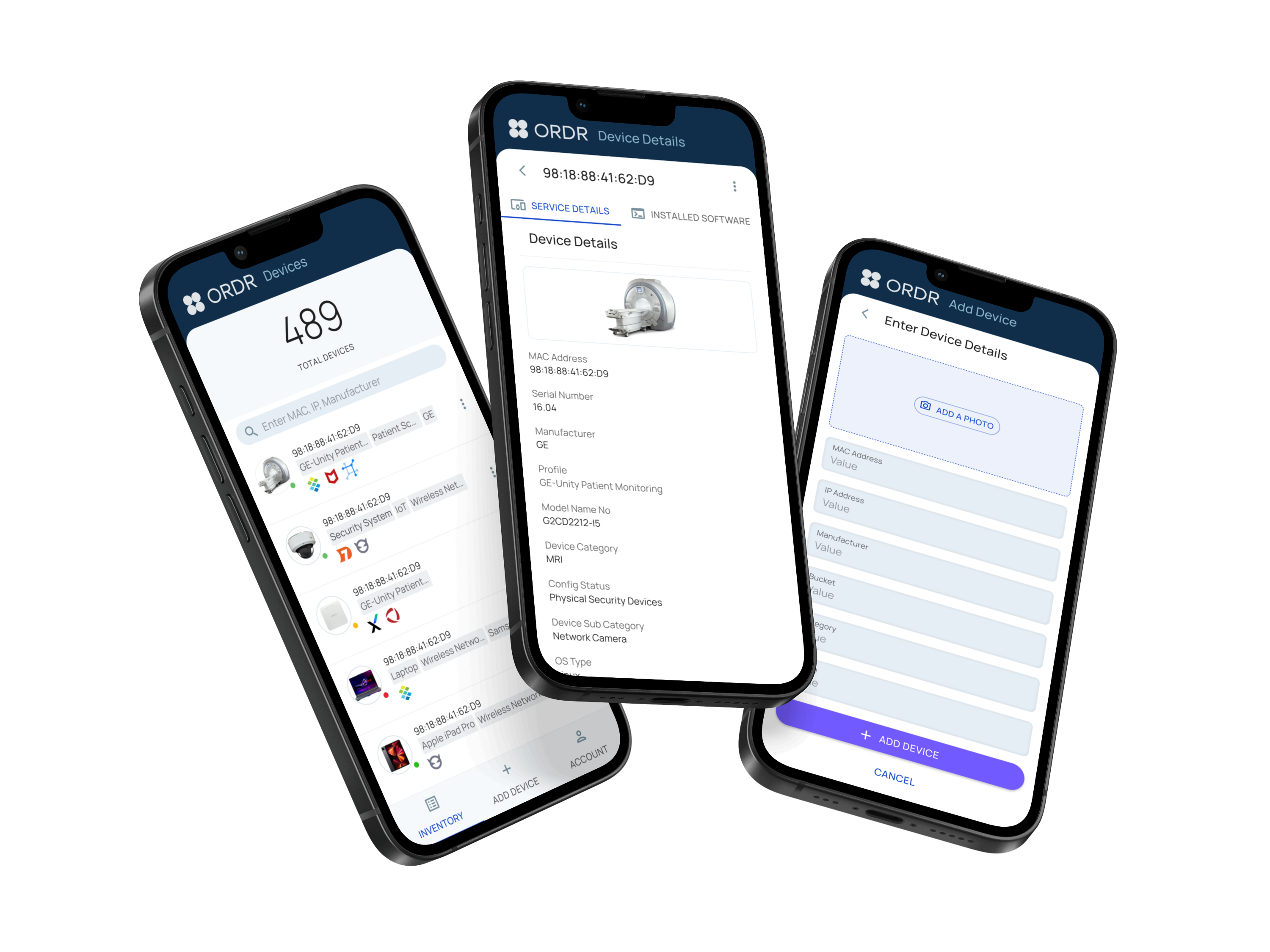
Alice can view inventory, check device details, or add new assets directly from her phone. This ensures she has access to asset intelligence and vulnerability information in the field, without being tied to her desktop.
